On-Demand: Web Application Security: Beginner Edition Bootcamp
A beginner-friendly introduction to the Open Web Application Security Project® (OWASP) Top 10 vulnerabilities, where you will build a solid foundation in pentesting modern web applications with different attack tools.
Recordings of this bootcamp are now available as part of our annual subscription. Subscribe to enjoy:
Recordings of this bootcamp are now available as part of our annual subscription. Subscribe to enjoy:
- Access to all on-demand bootcamps and relevant labs, including this one
- 2000+ hands-on labs covering another 130+ subtopics
Write your awesome label here.
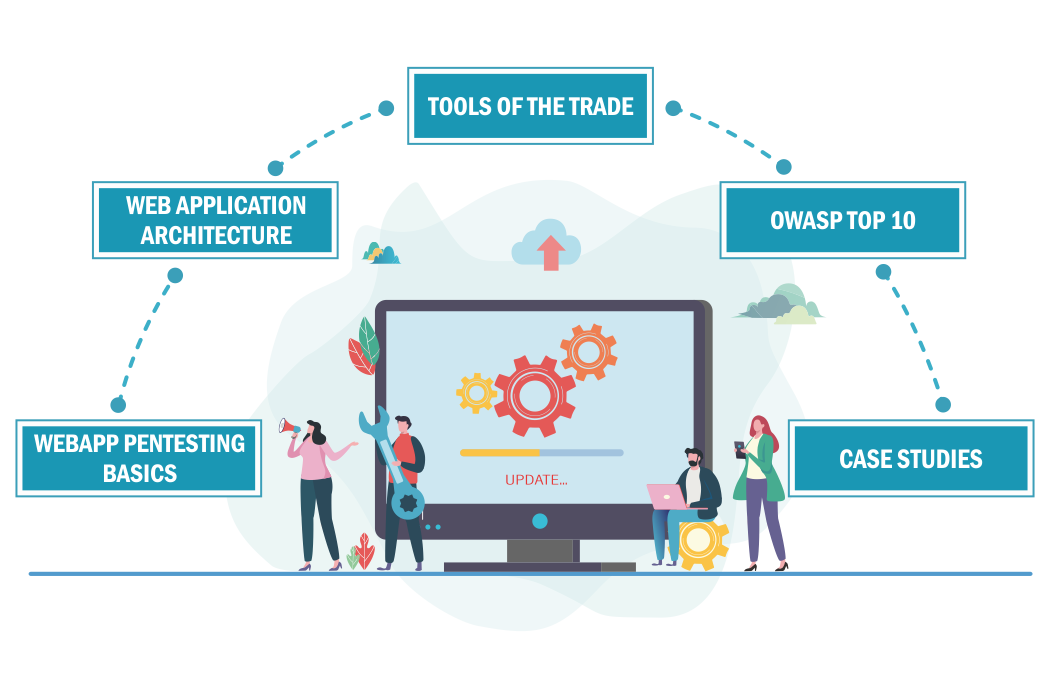
Module I: Modern Web Applications and Protocol Basics
-
Client-side Languages and Concepts
-
Server-side Concepts
-
Web Servers
-
Web Communication - HTTP verbs
-
HTTP request methods
-
HTTP response codes
-
HTTP headers and security
-
HTTP access control
-
HTTP authentication
-
HTTP cookies
-
HTTPS vs HTTP
-
Data Storage - Database Servers
-
SQL
-
NoSQL
-
Web Application Architecture
-
Monolithic architecture
-
Single page applications
-
Microservices
-
Serverless architecture
Module II: Reconnaissance Basics
-
Domain Reconnaissance
-
Whois lookup
-
DNS reconnaissance
-
Network Scanning and Live Host Identification
-
Open Ports and Running Services
-
Identifying Architectures, Operating Systems and Frameworks
-
Spidering/Crawling Websites
-
Performing Directory Enumeration
-
Discovering Protected Resources
Module III: Tools of the Trade
-
Enumerating Common/Framework-specific Directories
-
DIRB
-
DirBuster
-
Burp Suite
-
OpenDoor
-
Crawling Web Pages
-
ZAP
-
HTTrack
-
Burp Suite
-
Identifying Web Application Vulnerabilities with Scanners
-
Nikto
-
OpenVAS
-
Wapiti
-
Vega
-
OWASP OWTF
-
XSS Scanner
-
XSSer
-
Attacking Database Servers
-
sqlmap
-
jSQL
-
BBQSQL
-
A1 Injection Attacks
-
SQL Injection
-
NOSQL Injection
-
OS Command Injection
-
Code Injection
-
A2 Broken Authentication
-
Weak Credentials
-
Default Credentials
-
SQL Injection
-
Cookie Manipulation
-
Parameter Tampering
-
A3 Sensitive Data Exposure
-
Plain Text Transmission (HTTP/FTP/SMTP)
-
Presence of .git Directory
-
Presence of Debugging Utilities
-
Installation Files/README
-
Backup Directory/Log Directories
-
Lack of Custom Error Pages
-
A4 XML External Entity
-
Classic XXE
-
Error Based XXE
-
Blind XXE
-
A5 Broken Access Control
-
Path Traversal
-
Remote File Inclusion
-
Insecure Direct Object Reference
-
Client-Side Checks
-
Missing/Improper Functional Level Access Control
-
Missing HTTP Method-specific Access Control on Resources
-
CORS Misconfiguration
-
A6 Security Misconfigurations
-
Management Applications with Weak/Default Credentials
-
Directory Listing Enabled
-
Disabled Security Features
-
Poor Error Handling
-
A7 Cross-Site Scripting
-
Reflected Cross-Site Scripting
-
Stored Cross-Site Scripting
-
DOM Based Cross-Site Scripting
-
A8 Insecure Deserialization
-
Remote Code Execution
-
Denial of Service
-
A9 Using Components with Known Vulnerabilities
-
A10 Insufficient Logging & Monitoring
Module V: Real World Attacks
-
Case Study
-
Laravel Unserialize RCE (CVE-2018-15133)
-
Rails DoubleTap RCE (CVE-2019-5418, CVE-2019-5420)
-
Jquery-File-Upload (CVE-2018-9206)
-
Drupalgeddon2 (CVE-2018-7600)
Prerequisites
1. A basic knowledge of computers and networking
2. Familiarity with the Linux operating system
2. Familiarity with the Linux operating system
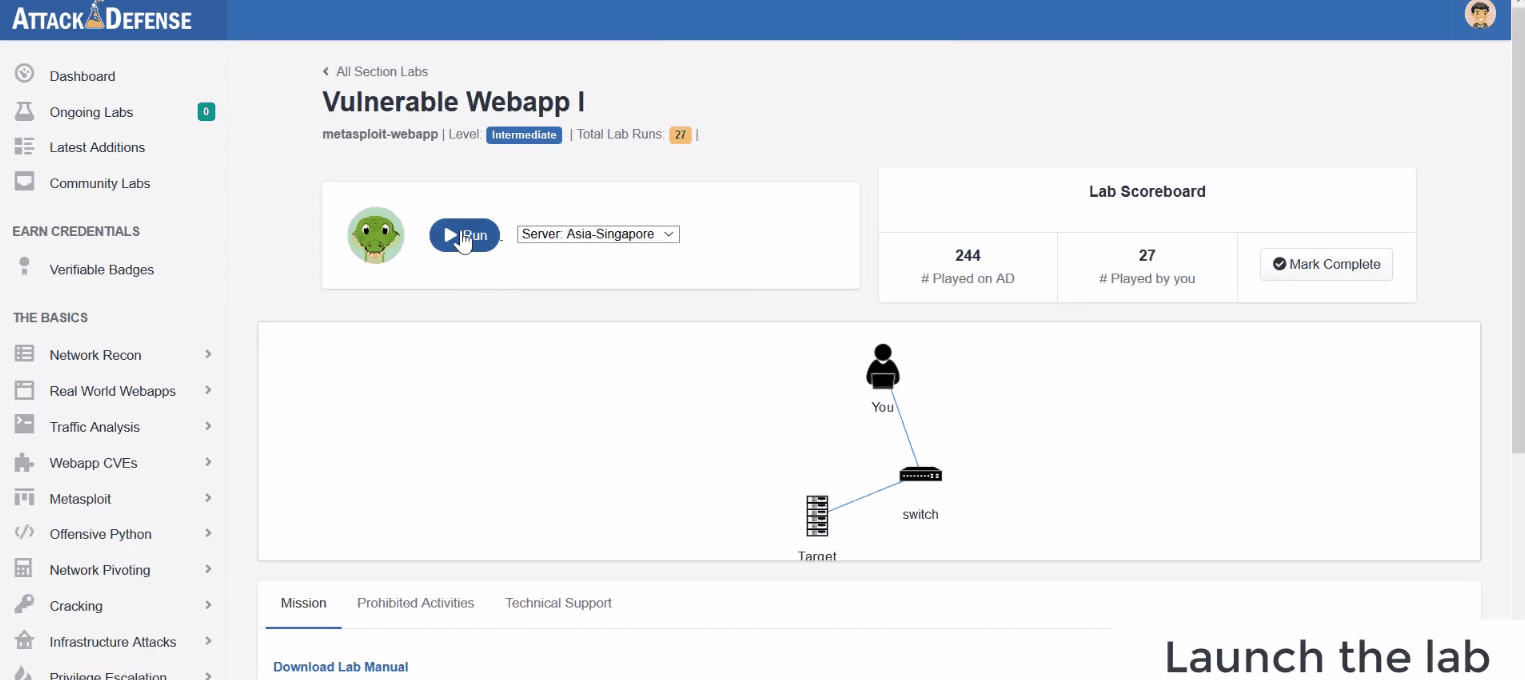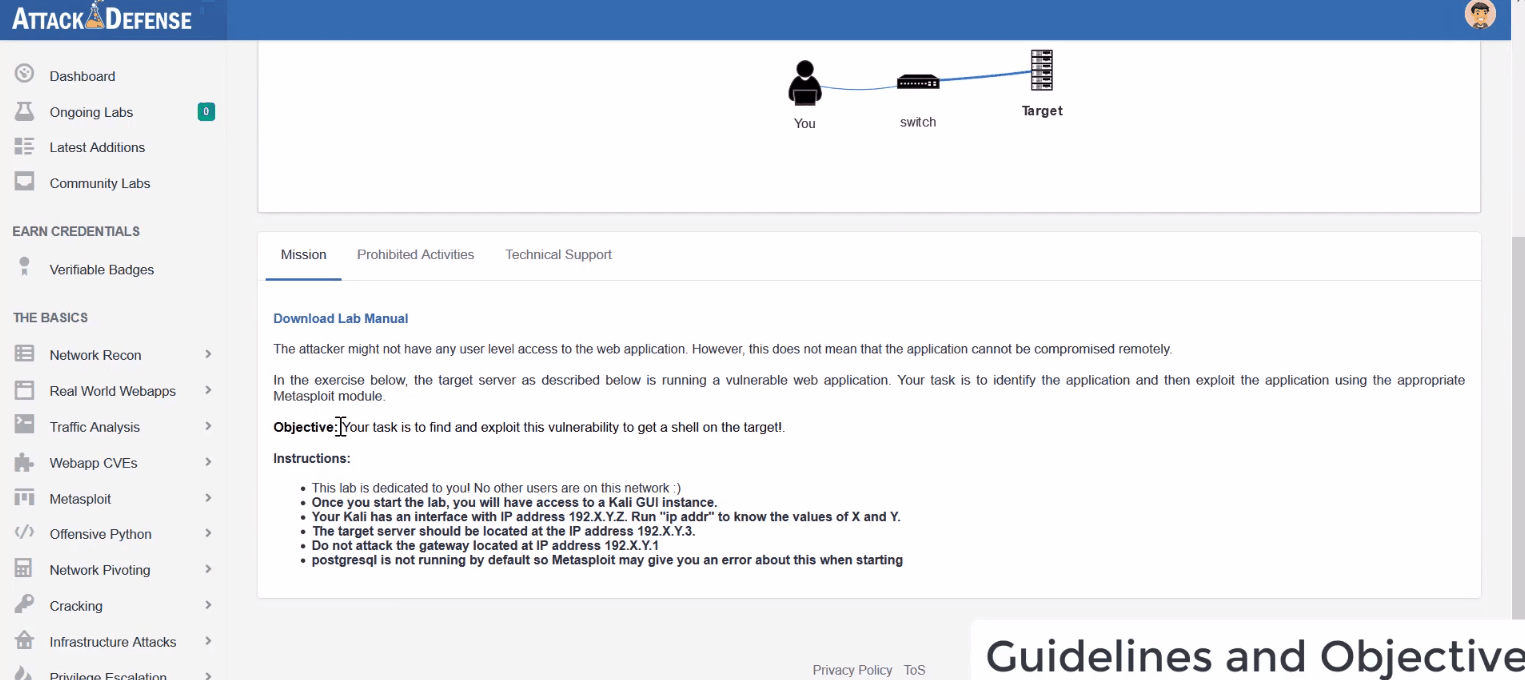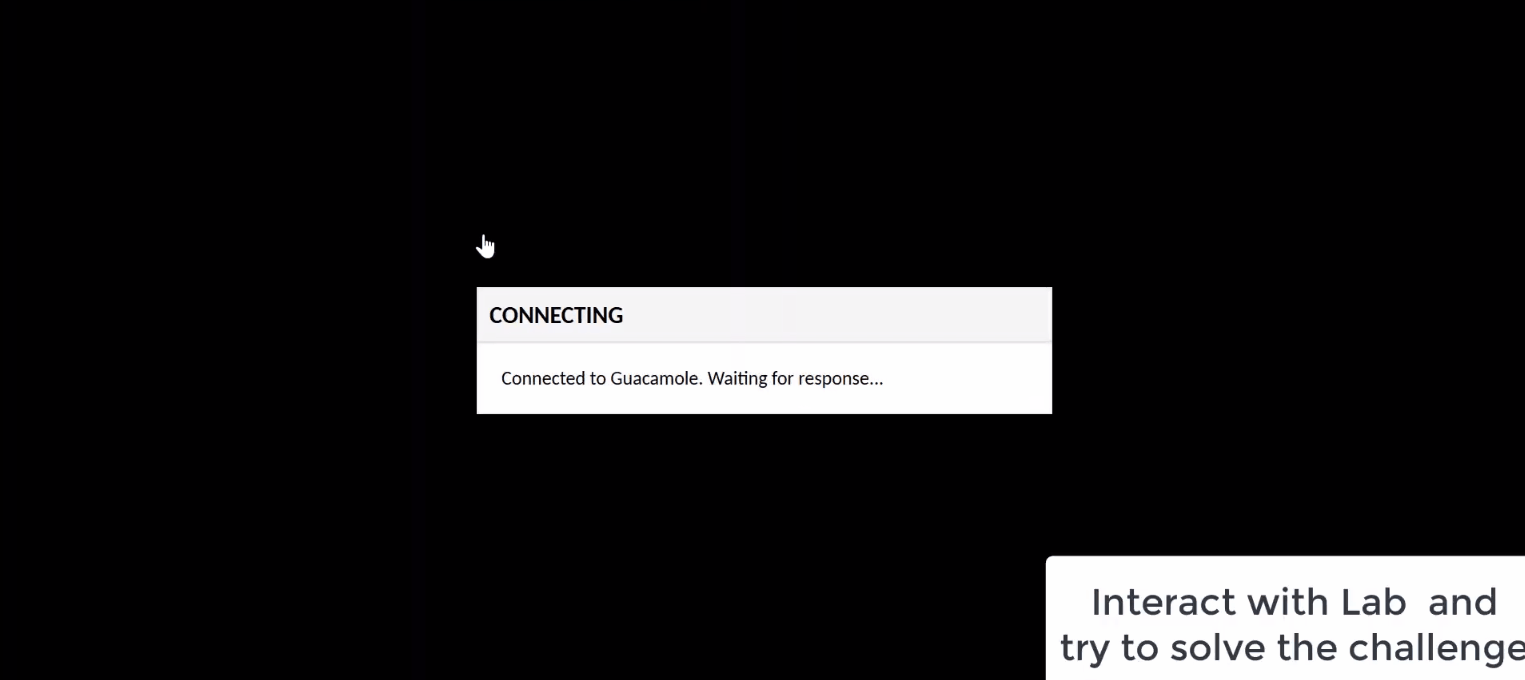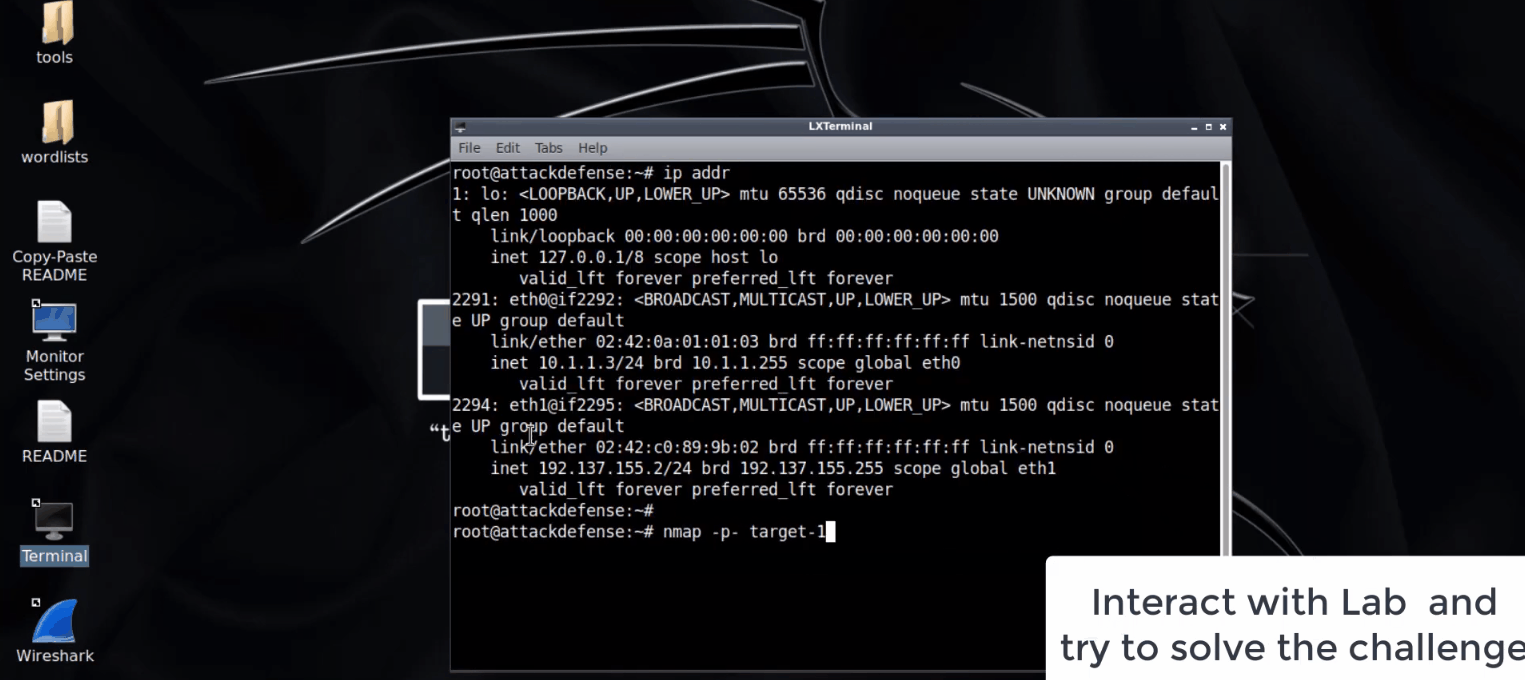
Accessible via our AttackDefense lab platform
Upon logging in to the AttackDefense lab platform, annual subscribers will be able to access recordings of all our on-demand bootcamps and associated labs.
Subscribe to access bootcamp recordings and more!
Meet the instructor
Jeswin Mathai
He has published his work at DEFCON China, RootCon, Blackhat Arsenal, and Demo labs (DEFCON). He has also been a co-trainer in classroom trainings conducted at HITB, RootCon, OWASP NZ Day. He has a Bachelor degree from IIIT Bhubaneswar. He was the team lead at InfoSec Society IIIT Bhubaneswar in association with CDAC and ISEA, which performed security auditing of government portals, conducted awareness workshops for government institutions. His area of interest includes Malware Analysis and Reverse Engineering, Cryptography, WiFi security, and Web Application Security.
Jeswin Mathai - Instructor
Get informed about future bootcamps!
Thank you!