Attacking and Defending Azure AD Cloud: Beginner's Edition [Jan 2023]
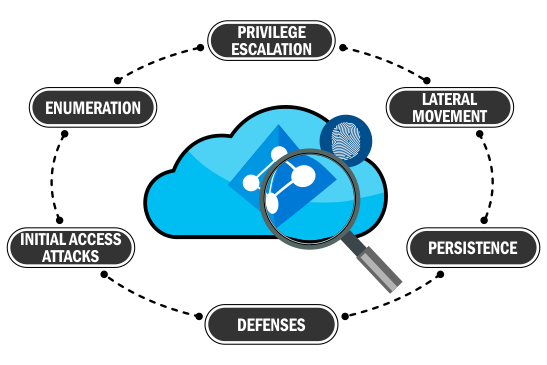
Upgrade to one of the most coveted Cloud skills – Azure Active Directory (AD) Security. Train in Azure pentesting, Red Teaming and defense in multiple live Azure tenants and hybrid infrastructure. Earn the Certified Az Red Team Professional (CARTP) certification.

Enrollment ends in:
Build Your Cybersecurity Credentials
Live Session Schedule
Prerequisites
1. Basic understanding of Azure AD is desired but not mandatory.
2. System with 4 GB RAM and ability to install OpenVPN client and RDP to Windows boxes.
3. Privileges to disable/change any antivirus or firewall.
2. System with 4 GB RAM and ability to install OpenVPN client and RDP to Windows boxes.
3. Privileges to disable/change any antivirus or firewall.
Meet the instructor
Nikhil Mittal
Nikhil Mittal is a hacker, infosec researcher, speaker and enthusiast. His area of interest includes red teaming, active directory security, attack research, defense strategies and post exploitation research. He has 12+ years of experience in red teaming.
He specializes in assessing security risks at secure environments that require novel attack vectors and "out of the box" approach. He has worked extensively on Active Directory, Azure AD attacks, defense and bypassing detection mechanisms and Offensive PowerShell for red teaming. He is creator of multiple tools like Nishang, a post exploitation framework in PowerShell, Deploy-Deception a framework for deploying Active Directory deception and RACE toolkit for attacking Windows ACLs. In his spare time, Nikhil researches on new attack methodologies and updates his tools and frameworks.
Nikhil has held trainings and bootcamps for various corporate clients (in US, Europe and SE Asia), and at the world’s top information security conferences. He has spoken/trained at conferences like DEFCON, BlackHat, BruCON and more.
He blogs at https://www.labofapenetrationtester.com/
He specializes in assessing security risks at secure environments that require novel attack vectors and "out of the box" approach. He has worked extensively on Active Directory, Azure AD attacks, defense and bypassing detection mechanisms and Offensive PowerShell for red teaming. He is creator of multiple tools like Nishang, a post exploitation framework in PowerShell, Deploy-Deception a framework for deploying Active Directory deception and RACE toolkit for attacking Windows ACLs. In his spare time, Nikhil researches on new attack methodologies and updates his tools and frameworks.
Nikhil has held trainings and bootcamps for various corporate clients (in US, Europe and SE Asia), and at the world’s top information security conferences. He has spoken/trained at conferences like DEFCON, BlackHat, BruCON and more.
He blogs at https://www.labofapenetrationtester.com/
Nikhil Mittal - Principal Instructor
Can't attend this bootcamp? Get informed about future bootcamps!
Thank you!